XDRNET: Active Defense for Enterprise of Things
Making Cybersecurity
Work For You

- All infrastructure protection (IT/OT/IoT)
- Continuous network monitoring
- Agent less
- Dark Web Analysis
- Easy installation and use
- Reduce costs
Our Product
XDRNet
Detects threats at earlier stages than other devices.
Multiple notification systems and immediate alerting.
Monitors the Dark Web for leaked credentials.
Automation in Targeted Attack processes.
Immediate isolation and blocking of the threat.
Cloud
Data Center
Enterprise
IoT
OT
Start your Active Defense plan today.
Description
Technical Specifications
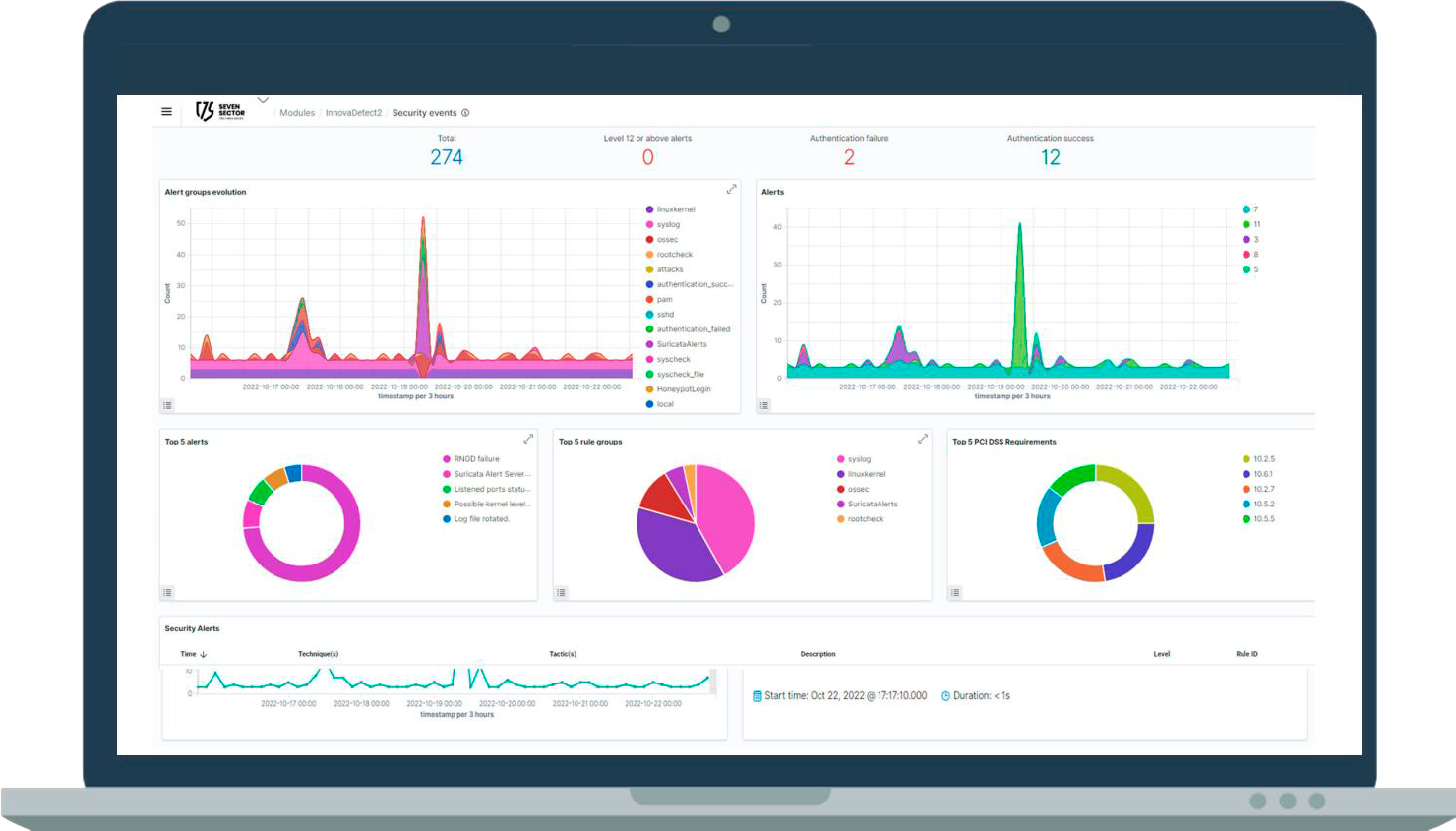
Advanced Threat Detection through multiple systems
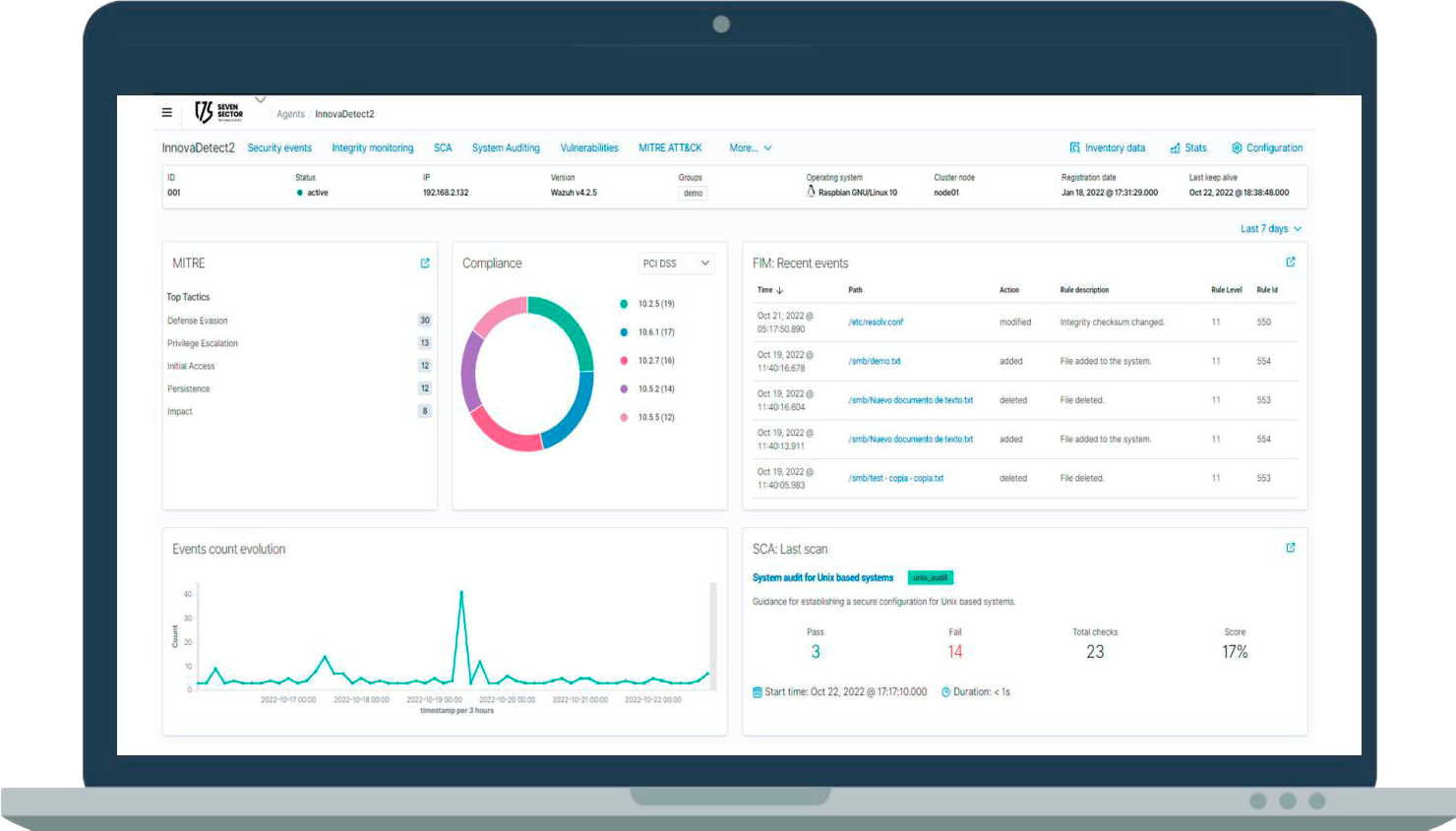
Real-Time Detection of any type of threat connected to your IT, Cloud, IoT network, or in industrial segments (OT).
We detect any creation, modification, or deletion on audited folders that simulate the company's document structure.
High interaction with the different emulated Operating Systems or services that allow obtaining Indicators of Compromise (IoC).
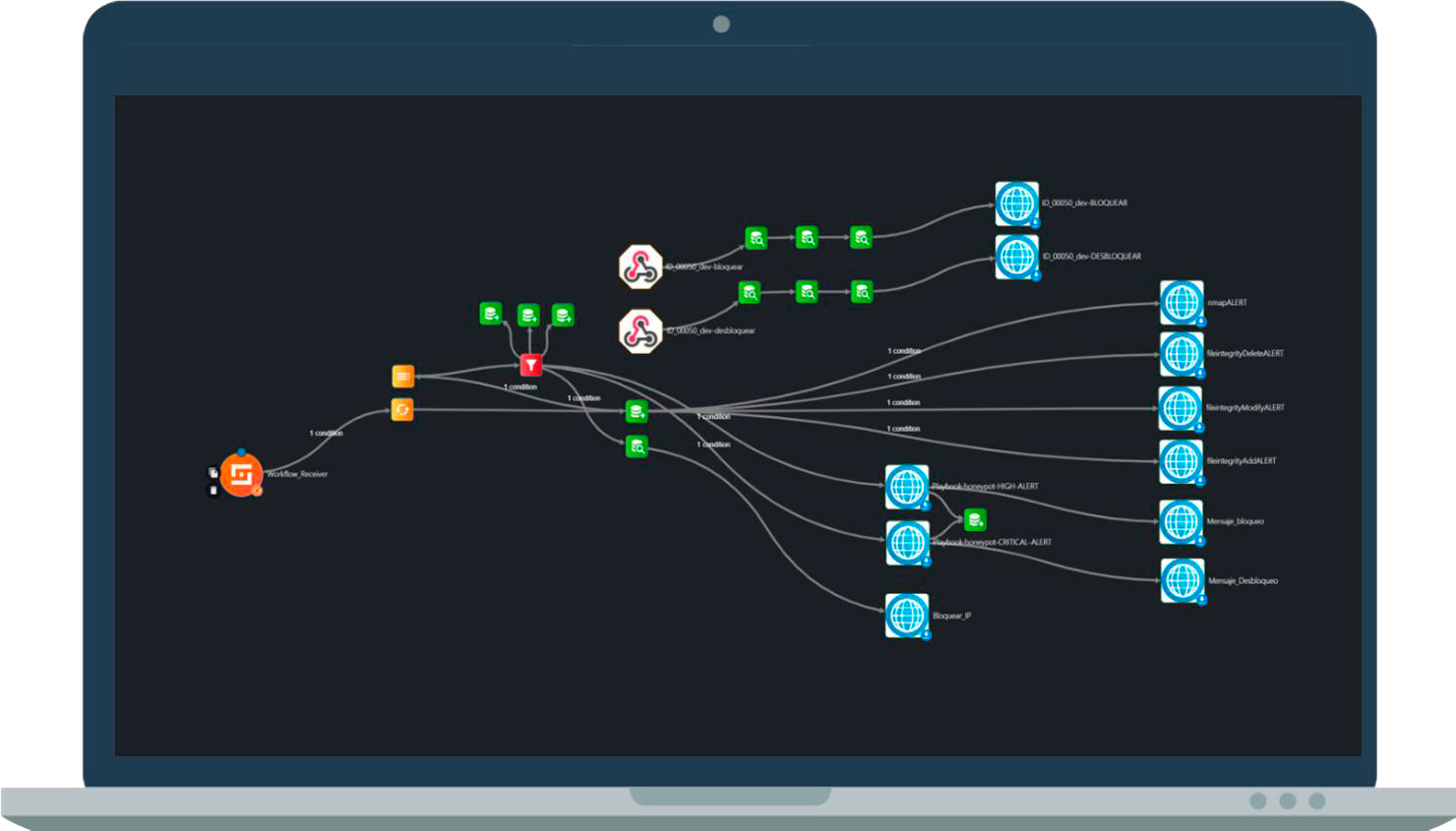
“XDRNET enables the generation and customization of playbooks, reducing the response time to threats’ impact. Its integration with various systems allows for both action automation and blocking by an operator or technician with just one click.”
Immediate Alert after detecting compromise in the systems
Identification of the attacker with the compromised device data, facilitating their identification at the moment of intrusion.
Recommendation of actions for containment or analysis of the Alert. Threat isolation in just one click.
You will only receive alerts in which intrusion has actually been detected, eliminating the high rate of False Positives.
XDRNET integrates with multiple ‘Push’ notification systems, so you can receive the alert on mobile phones as well as other types of devices. This allows us to respond immediately when there is a real compromise in the network.
Monitoring of credentials on the Dark Web
We dynamically search for any leakage or sale of data in channels, forums, or publications on the Dark Web.
We incorporate exposed credentials into our database to detect Targeted Attacks against your organization.
We have over 3.2 billion combinations of legitimate user-password pairs in our database to analyze the results.
“The Threat Intelligence team at XDRNET continuously monitors the Dark Web, searching for credentials for sale that have been fraudulently obtained to increase our database with over 3.2 trillion unique user/password combinations.”
Automation of actions against Targeted Attacks
We understand the context of the company and isolate the network of the compromised device, preventing lateral movements.
We examine all generated alerts, reporting any anomalous behaviors that require review by the IT team.
We generate alerts that allow integration with other Orchestration elements, expanding the detail of the IoC.
“XDRNET allows for the generation and customization of playbooks, reducing the time to action in response to a threat. Its integration with different systems enables both action automation and blocking by an operator or technician with just one click.”
Threat isolation without agent installation
We are able to isolate a threat in Industrial environments as well as communications between PLCs, SCADA, Robots, ... without impacting the rest of the network.
We protect hybrid segments, Cloud or On-premise, where communication between them is complex.
We isolate the detected threat using techniques that allow blocking connections from the device, without the need to install any agents.
We are the only technology capable of isolating a threat without any additional installation.
“The purpose we have with our R&D is the foundation of our main goal. We aim to drive change and guide our clients in their own security transformation, in a close and personal manner. Thanks to our R&D, we provide specific solutions and services to meet new needs.”
Hiram Fernández, Chief Executive Officer, SEVEN SECTOR TECHNOLOGIES
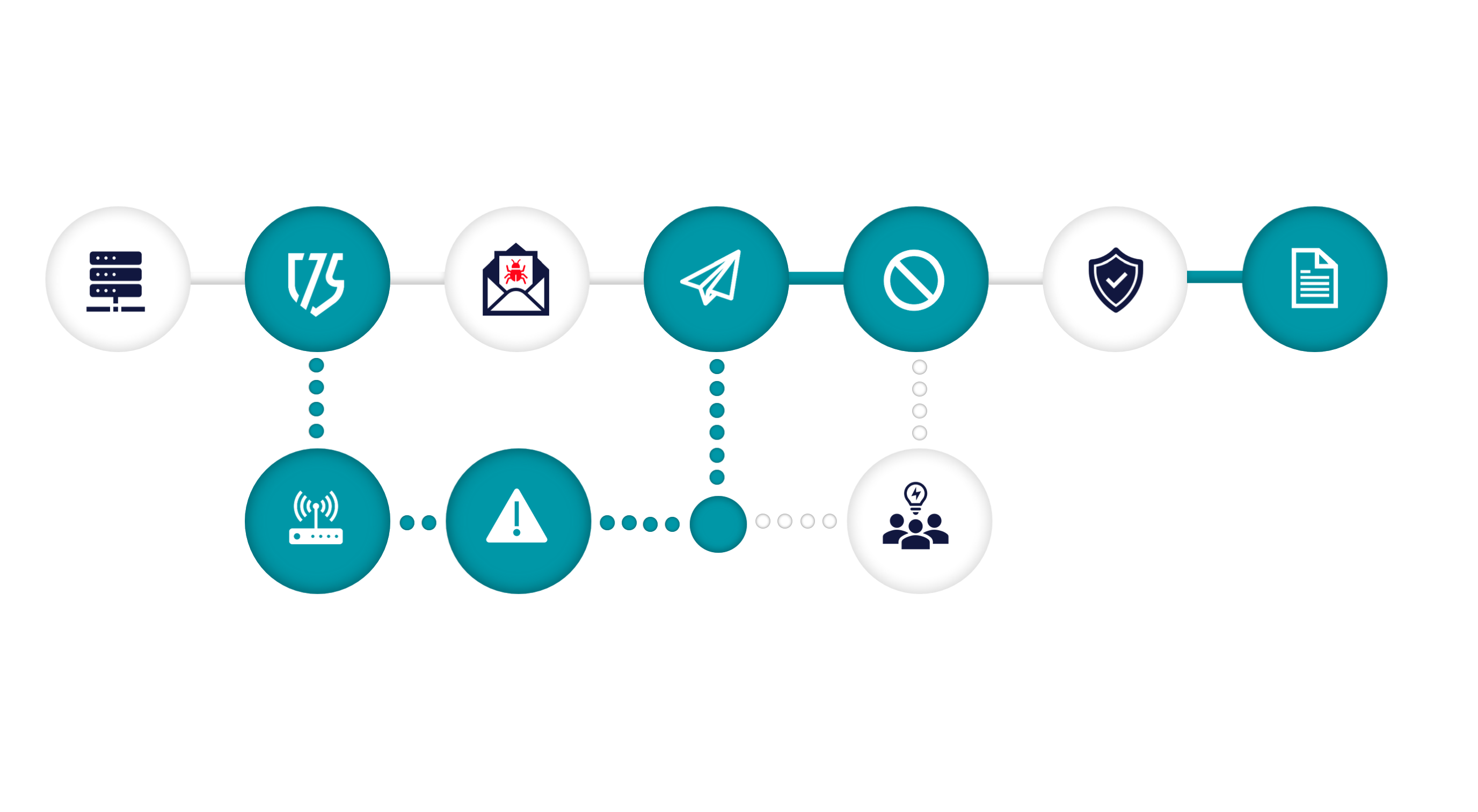
CUSTOMER JOURNEY
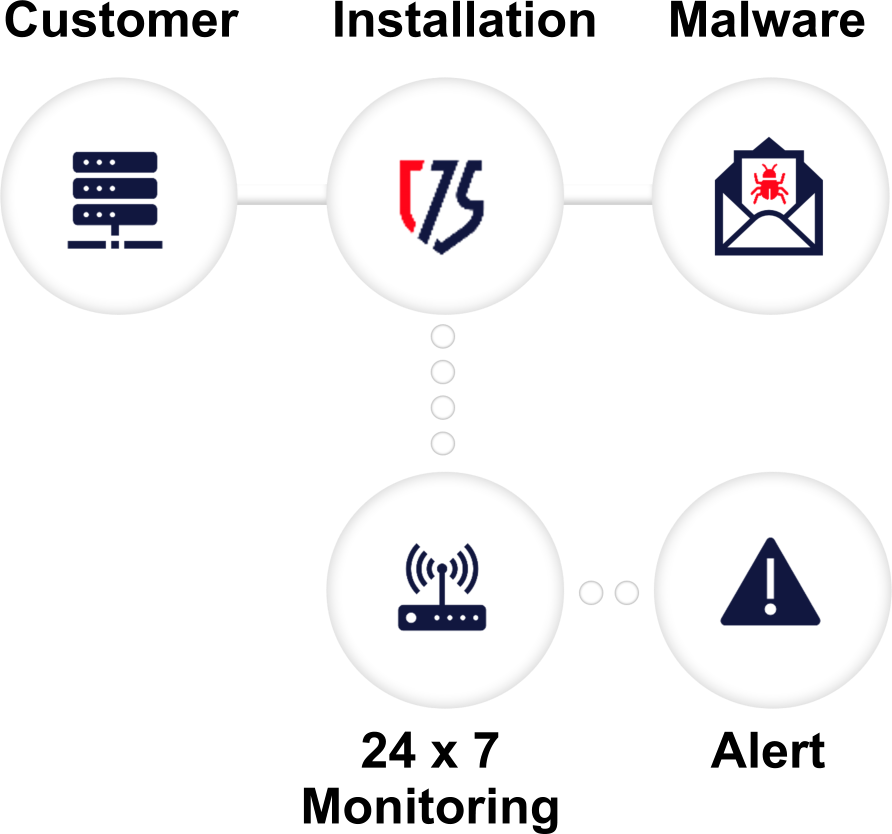


If something is detected, the SOC team responds with the established procedure (playbooks) that include options according to the license level, such as:
- Immediate warning.
- Blocking or isolating the threat.
FAQ
Frequently Ask Questions
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Clients we have worked with
Testimonials
What they say about us



Start your Active Defense plan today
BASIC
- Network Detection System
- File Integrity
- Operating Systems Simulation
- Real Time Notification
PRO
- Basic +
- Data Leak Monitoring
- Threat Blocking
- Multi VLAN Monitoring
Do you need help?
If you have any questions or need more information, please contact us. We are here to help you.